Professor
College of Computer Science and Technology
Nanjing University of Aeronautics and Astronautics
29 Jiangjun Boulevard
Nanjing 211106, China
Office: College Building #236
Email: hhan@nuaa.edu.cn
Short Biography
Dr. Hao Han is a Professor in the College of Computer Science and Technology, Nanjing University of Aeronautics and Astronautics (NUAA). He received his Ph.D. degree from the College of William and Mary in 2014, advised by Prof. Qun Li. Prior to joining NUAA, Dr. Han worked at IBM China Research Laboratory, Microsoft Research Asia, and Intelligent Automation Inc., US. He currently leads the Security of Smart Systems Lab (S3Lab) at NUAA. He received the Jiangsu Distinguished Professor(江苏省特聘教授), the Six Talent Peaks Project of Jiangsu Province (江苏省六大人才高峰), and the ACM Nanjing Rising Star Award. Dr. Han's research has been mainly focused on System Security in the the practice of protecting intelligent systems from unauthorized access, tampering, or data leakage. He is a member of CCF, IEEE and ACM.
Publication
*Tips: use doi2bib to convert DOI to BibTeX entryJournal Articles
-
[TDSC] MACO: Model Anti-extraction via Compiler Obfuscation
Yang Li, Minghui Li, Hao Han, Liming Fang
IEEE Transactions on Dependable and Secure Computing, accepted, 2025 (CCF A)
DOI: 10.1109/TDSC.2025.3601219
-
[TIFS] UTRDCL: Stealthy DCL-Based Obfuscation and Its Attacks and Defenses in Android
Xin Zhao, Hao Han, Hao Wu, Sheng Zhong, Fengyuan Xu
IEEE Transactions on Information Forensics and Security, vol. 20, pp. 9068-9083, 2025 (CCF A)
DOI: 10.1109/TIFS.2025.3601338
-
[TMC] Robust and Effort-Efficient Image-Based Indoor Localization with Generative Features
Zhenhan Zhu, Yanchao Zhao, Maoxing Tang, Yanling Bu, Hao Han
IEEE Transactions on Mobile Computing, vol. 24, no. 07, pp. 6394-6412, 2025 (CCF A)
DOI: 10.1109/TMC.2025.3541045
-
[CJE] Design, Realization, and Evaluation of FastDIM to Prevent Memory Corruption Attacks
Jian Huang, Yanbo Li, Hao Han
Chinese Journal of Electronics, vol. 34, no. 4, pp. 1233–1246, 2025
DOI: 10.23919/cje.2024.00.218
-
[WN] Quest: Instant Questionnaire Collection from Handshake Messages using WLAN
Xiaojun Zhu, and Hao Han
Wireless Networks, vol. 30, no. 4, pp. 2081–2098, Jan. 2024 (CCF C)
DOI: 10.1007/s11276-023-03645-6
-
[TMC] RescQR: Enabling Reliable Data Recovery in Screen-Camera Communication System
Hao Han, Kunming Xie, Tongyu Wang, Xiaojun Zhu, Yanchao Zhao, Fengyuan Xu
IEEE Transactions on Mobile Computing, vol. 23, no. 5, pp. 3510-3522, May 2024 (CCF A)
DOI: 10.1109/TMC.2022.3207745
-
[TMC] LEAP: TrustZone Based Developer-Friendly TEE for Intelligent
Mobile Apps
Lizhi Sun, Shuocheng Wang, Hao Wu, Yuhang Gong, Fengyuan Xu, Yunxin Liu, Hao Han, and Sheng Zhong
IEEE Transactions on Mobile Computing, vol. 22, no. 12, pp. 7138-7155, Dec. 2023 (CCF A)
DOI: 10.1109/TMC.2023.3277212
-
[TIOT] UltraSnoop: Placement-agnostic Keystroke Snooping via Smartphone-based Ultrasonic Sonar
Yanchao Zhao, Yiming Zhao, Si Li, Hao Han, and Lei Xie
ACM Transactions on Internet of Things, vol. 4, no. 4, article 22, pp. 1-24, Nov. 2023
DOI: 10.1145/3614440
-
[WCMC] User-Level Membership Inference for Federated Learning in
Wireless Network Environment
Yanchao Zhao, Jiale Chen, Jiale Zhang, Zilu Yang, Huawei Tu, Hao Han, Kun Zhu and Bing Chen
Wireless Communications and Mobile Computing, vol. 2021, pp. 1-17, Oct. 2021 (CCF C)
DOI: 10.1155/2021/5534270
-
[TII] Secure Transmission of Compressed Sampling Data Using Edge
Clouds
Yushu Zhang, Ping Wang, Liming Fang, Xing He, Hao Han and Bing Chen
IEEE Transactions on Industrial Informatics, vol. 16, no. 10, pp. 6641-6651, 2020
DOI: 10.1109/TII.2020.2966511
-
[TPDS] Efficient Protocols for Collecting Histograms in Large-scale
RFID Systems
Lei Xie, Hao Han, Qun Li, Jie Wu, and Sanglu Lu
IEEE Transactions on Parallel and Distributed Systems, vol. 26, no. 9, pp. 2421-2433, 2015 (CCF A)
DOI: 10.1109/TPDS.2014.2357021
-
[TON] Design, Realization, and Evaluation of DozyAP for
Power-Efficient Wi-Fi Tethering
Hao Han, Yunxin Liu, Guobin Shen, Yongguang Zhang, Qun Li and Chiu C. Tan
IEEE/ACM Transactions on Networking, vol. 22, No. 5, pp. 1672-1685, 2014 (CCF A)
DOI: 10.1109/TNET.2013.2283636
-
[TVT] VProof: Lightweight Privacy-Preserving Vehicle Location
Proofs
Yifan Zhang, Chiu C. Tan, Fengyuan Xu, Hao Han, Qun Li
IEEE Transactions on Vehicular Technology, vol. 64, No. 1, pp. 378-385, 2015
DOI: 10.1109/TVT.2014.2321666
-
[TVT] VR-Defender: Self-Defense Against Vehicular Rogue APs for
Drive-Thru Internet
Hao Han, Fengyuan Xu, Chiu C. Tan, Yifan Zhang, and Qun Li,
IEEE Transactions on Vehicular Technology, vol. 63, No. 8, pp. 3927-3934, 2014
DOI: 10.1109/TVT.2014.2311015
-
[TPDS] A Timing Based Scheme for Rogue AP Detection
Hao Han, Bo Sheng, Chiu C. Tan , Qun Li, and Sanglu Lu
IEEE Transactions on Parallel and Distributed Systems, vol. 22, No. 11, pp. 1912-1925, 2011 (CCF A)
DOI: 10.1109/TPDS.2011.125
-
[AAAI'26] Enhancing All-to-X Backdoor Attacks with Optimized Target Class Mapping
Lei Wang, Yulong Tian, Hao Han, Fengyuan Xu
The 40th Annual AAAI Conference on Artificial Intelligence, Singapore, JAN 20–27 2026 (CCF A)
-
[SC'25] Exploring and Mitigating Failure Behavior of Large Language Model Training Workloads in HPC Systems
Pengfei Yu, Jingjing Gu, Hao Han, Dazhong Shen, Bao Wen, Yang Liu,
International Conference for High Performance Computing, Networking, Storage, and Analysis, St. louis, MO, NOV 16–21 2025 (CCF A)
-
[ICSME'25] ADPP: Automated Data-centric Program Partitioning
Xuming Jin, Hao Han
IEEE International Conference on Software Maintenance and Evolution, Auckland, New Zealand, Sep. 7–12 2025 (CCF B)
-
[WWW'25] Instruction Vulnerability Prediction for WebAssembly with Semantic Enhanced Code Property Graph
Bao Wen, Jingjing Gu, Hao Han, Pengfei Yu, Yang Liu,
The Web Conference, Sydney, Australia, April 28-May 2 2025 (CCF A)
-
[ISSRE'24] REDLC: Learning-driven Reverse Engineering for Deep Learning Compilers
Minghui Li, Yang Li, Hao Han, Xiaopeng Ke, Tongyu Wang, Fengyuan Xu, and Liming Fang
IEEE International Symposium on Software Reliability Engineering, Tsukuba, Japan, Oct.28-31 2024 (CCF B)
DOI: 10.1109/ISSRE62328.2024.00029.
-
[ICASSP'24] Towards Faster End-to-End Data Transmission over Voice Channels
Weijun Zhang, Hao Han, Mingwei Li, and Yulong Tian
IEEE International Conference on Acoustics, Speech and Signal Processing, Seoul, Korea, Apr. 14-19 2024 (CCF B)
DOI: 10.1109/ICASSP48485.2024.10447419
-
[MSN'23] ShuffleCAN: Enabling Moving Target Defense for Attack Mitigation on Automotive CAN
Huiping Qian, Hao Han, Xiaojun Zhu and Fengyuan Xu
IEEE International Conference on Mobility, Sensing and Networking, Nanjing, China, Dec.14-16 2023 (CCF C)
DOI: 10.1109/MSN60784.2023.00059
-
[ISSRE'23] SAPPX: Securing COTS Binaries with Automatic Program Partitioning for Intel SGX
Jiawei Huang, Hao Han, Fengyuan Xu, Bing Chen
IEEE International Symposium on Software Reliability Engineering, Florence, Italy, Oct.9-12 2023 (CCF B)
DOI: 10.1109/ISSRE59848.2023.00016
-
[IWQoS'22] Privacy-Preserving and Robust Federated Deep Metric
Learning
Yulong Tian, Xiaopeng Ke, Zeyi Tao, Shaohua Ding, Fengyuan Xu, Qun Li, Hao Han, Sheng Zhong, and Xinyi Fu
IEEE/ACM International Symposium on Quality of Service, Virtual Conference, June 2022 (CCF B)
DOI: 10.1109/IWQoS54832.2022.9812909
-
[IWQoS'21] ChirpMu: Chirp Based Imperceptible Information
Broadcasting with Music
Yu Wang, Xiaojun Zhu and Hao Han
IEEE/ACM International Symposium on Quality of Service, Virtual Conference, June 2021 (CCF B)
DOI: 10.1109/IWQOS52092.2021.9521353
-
[ICCCN'20] Beyond Model-Level Membership Privacy Leakage: an
Adversarial Approach in Federated Learning
Jiale Chen, Jiale Zhang, Yanchao Zhao, Hao Han, Kun Zhu and Bing Chen
International Conference on Computer Communications and Networks, Virtual Conference, August 2020 (CCF C)
DOI: 10.1109/ICCCN49398.2020.9209744
-
[SEC'20] TAES: Two-factor Authentication with End-to End Security
against VoIP Phishing
Dai Hou, Hao Han and Ed Novak
IEEE/ACM Symposium on Edge Computing (SEC), San Jose, CA, November 2020
DOI: 10.1109/SEC50012.2020.00049
-
[SEC'20] FareQR: Fast and Reliable Screen-Camera Transfer System
for Mobile Devices using QR Code
Tongyu Wang, Hao Han, Zijie Wang
IEEE/ACM Symposium on Edge Computing (SEC), San Jose, CA, November 2020
DOI: 10.1109/SEC50012.2020.00053
-
[SpaCCS'20] DFspliter: Data Flow Oriented Program Partitioning
against Data Stitching Attacks
Chenyu Zhao and Hao Han
International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage, Nanjing, China, Dec. 2020
DOI: 10.1007/978-3-030-68851-6_6
-
[SpaCCS'20] Revisiting Attacks and Defenses in Connected and
Autonomous Vehicles
Ziyan Fang, Weijun Zhang Zongfei Li, Huaao Tang, Hao Han and Fengyuan Xu
International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage, Nanjing, China, Dec. 2020
DOI: 10.1007/978-3-030-68851-6_7
-
[MILCOM'18] Routing, Network Coding and TCP Support for Wideband HF
Communications
Tugba Erpek, Yalin E. Sagduyu, Yi Shi, Maice Costa, Kemal Davaslioglu, Hao Han, Daniel Fayette, Eric Johnson, Elizabeth Bentley, Clif Banner
IEEE Military Communications Conference (MILCOM), Los Angeles, CA, October 2018
DOI: 10.1109/MILCOM.2018.8599765
-
[RAID'17] VDF: Targeted Evolutionary Fuzz Testing of Virtual
Devices
Andrew Henderson, Heng Yin, Guang Jin, Hao Han and Hongmei Deng
International Symposium on Research in Attacks, Intrusions and Defenses (RAID), Atlanta, Georgia, September, 2017 (CCF B)
DOI: 10.1007/978-3-319-66332-6_1
-
[INFOCOM'16] AMIL: Localizing Neighboring Mobile Devices Through a
Simple Gesture
Hao Han, Shanhe Yi, Qun Li, Guobin Shen, Yixun Liu, and Ed Novak
IEEE Conference on Computer Communications (INFOCOM), San Francisco, CA, April, 2016 (CCF A)
DOI: 10.1109/INFOCOM.2016.7524392
-
[INFOCOM'14] Efficiently Collecting Histograms Over RFID
Tags
Lei Xie, Hao Han, Qun Li, Jie Wu, Sanglu Lu
IEEE Conference on Computer Communications (INFOCOM), Toronto, Canada, 2014 (CCF A)
DOI: 10.1109/INFOCOM.2014.6847934
-
[MOBISYS'12] DozyAP: Power-Efficient Wi-Fi Tethering
Hao Han, Yunxin Liu, Guobin Shen, Yongguang Zhang, and Qun Li
ACM International Conference on Mobile Systems, Applications, and Services (MOBISYS), Low Wood Bay, UK, June 2012 (CCF B)
DOI: 10.1145/2307636.2307675
-
[INFOCOM'11] Defending Against Vehicular Rogue APs
Hao Han, Fengyuan Xu, Chiu C. Tan, Yifan Zhang, and Qun Li
IEEE Conference on Computer Communications (INFOCOM), Shanghai, China, April 2011 (CCF A)
DOI: 10.1109/INFCOM.2011.5934960
-
[INFOCOM'10] Counting RFID Tags Efficiently and Anonymously
Hao Han, Bo Sheng, Chiu C. Tan, Qun Li, Weizhen Mao, and Sanglu Lu
IEEE Conference on Computer Communications (INFOCOM), San Diego, CA, April 2010 (CCF A)
DOI: 10.1109/INFCOM.2010.5461944
-
[INFOCOM'10] Efficient Tag Identification in Mobile RFID
Systems
Lei Xie, Bo Sheng, Chiu C. Tan, Hao Han, Qun Li, and Daoxu Chen
IEEE Conference on Computer Communications (INFOCOM), San Diego, CA, April 2010 (CCF A)
DOI: 10.1109/INFCOM.2010.5461949
-
[INFOCOM'09] A Measurement Based Rogue AP Detection Scheme
Hao Han, Bo Sheng, Chiu C. Tan, Qun Li, and Sanglu Lu
IEEE Conference on Computer Communications (INFOCOM), Rio de Janeiro, Brazil, April 2009 (CCF A)
DOI: 10.1109/INFCOM.2009.5062077
Teaching
Undergradute-Level Courses
- Operating Systems(中文), Spring 2019 - Present
- Principle of Computer’s Composition (English), Fall, 2019 - 2020
- Security in Computer System (English), Fall 2020 -
2023
- 2025,“中国网谷-华为杯”中国研究生网络安全创新大赛,全国二等奖
- 2024,“中国网谷-华为杯”中国研究生网络安全创新大赛,全国二等奖
- 2024,全国大学生信息安全竞赛(作品赛),全国二等奖
- 2022,中国高校计算机大赛网络技术挑战赛,全国总决赛二等奖
- 2022,全国大学生系统能力大赛操作系统设计赛, 优秀指导教师
- 2021,全国大学生信息安全竞赛(作品赛),全国二等奖
Projects
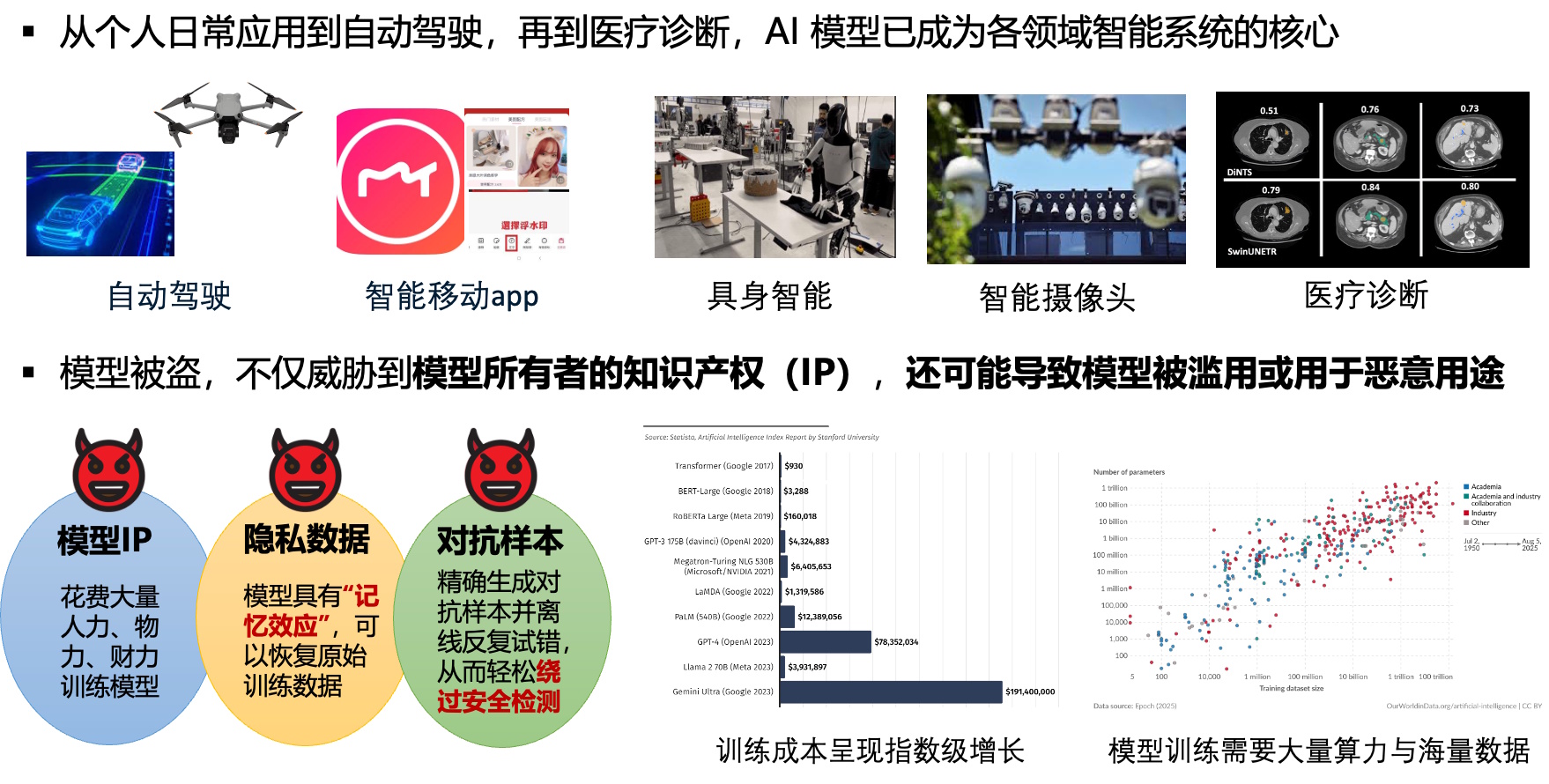
Model Stealing Attacks and Defenses for Deployed AI SystemsThis research investigates the emerging security threat of AI model stealing and reverse engineering in the context of modern deployment paradigms, where trained AI models are no longer confined to cloud servers but are increasingly deployed on end devices, including mobile phones, embedded systems, edge computing nodes, and even directly within Web browsers through technologies such as WebAssembly and JavaScript-based runtimes. While this deployment trend significantly improves latency, availability, and privacy by enabling local inference, it also exposes AI models to adversaries who can directly interact with, inspect, and manipulate the execution environment. As a result, proprietary models—often representing substantial intellectual property, data curation effort, and training cost—face serious risks from model extraction, parameter reconstruction, architecture inference, and functional imitation attacks. Existing defenses at the algorithmic level are often insufficient in these settings because attackers may gain access to the deployed model artifacts rather than relying solely on black-box queries. Our research focuses on developing new model stealing attacks and a system-level defense strategy that integrates deep learning compilers, binary rewriting, and trusted execution technologies to raise the bar against both static and dynamic model stealing attacks.
Program Hardening Framework Against Low-Level Exploitation
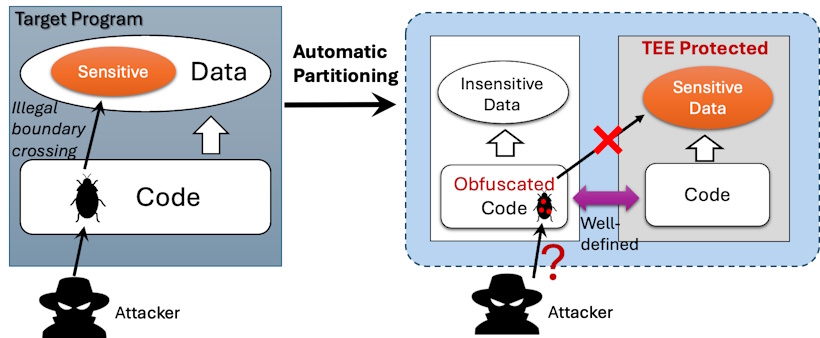
This research topic focuses on program hardening technologies that strengthen software systems against low-level exploitation such as memory corruption attacks. Program hardening seeks to raise the attacker’s cost by fundamentally altering how programs are structured, represented, and executed, rather than relying solely on vulnerability elimination. Within this scope, program partitioning, code obfuscation, and Trusted Execution Environments (TEEs) form three mutually reinforcing pillars. Program partitioning restructures applications by separating security-critical components from less trusted logic, thereby minimizing the attack surface. Obfuscation further complicates exploitation by obscuring control flow, data layouts, and memory access patterns, degrading the attacker’s ability to reliably construct exploits or reuse gadgets even in the presence of vulnerabilities. TEEs complement these software-level defenses by providing hardware-enforced isolation, ensuring that sensitive code and data remain protected even if an attacker gains root privileges.
Attacks and Defenses in Connected Autonomous Vehicles
With the development of the automotive industry, the security of connected and autonomous vehicles (CAVs) has become a hot research field in recent years. However, previous studies mainly focus on the threats and defending mechanisms from the networking perspective, while newly emerging attacks are targeting more core components of CAVs such as OS and AI. Therefore, the defense methods against these attacks are urgently needed. In this paper, we revisit emerging attacks and their technical countermeasures for CAVs in a layered inventory, including in-vehicle systems, V2X, and self-driving. This project aims to provide insights into potential new attack vectors and their countermeasures for CAVs. We hope to shed light on future research in this area.
Securing Industrial Control Systems
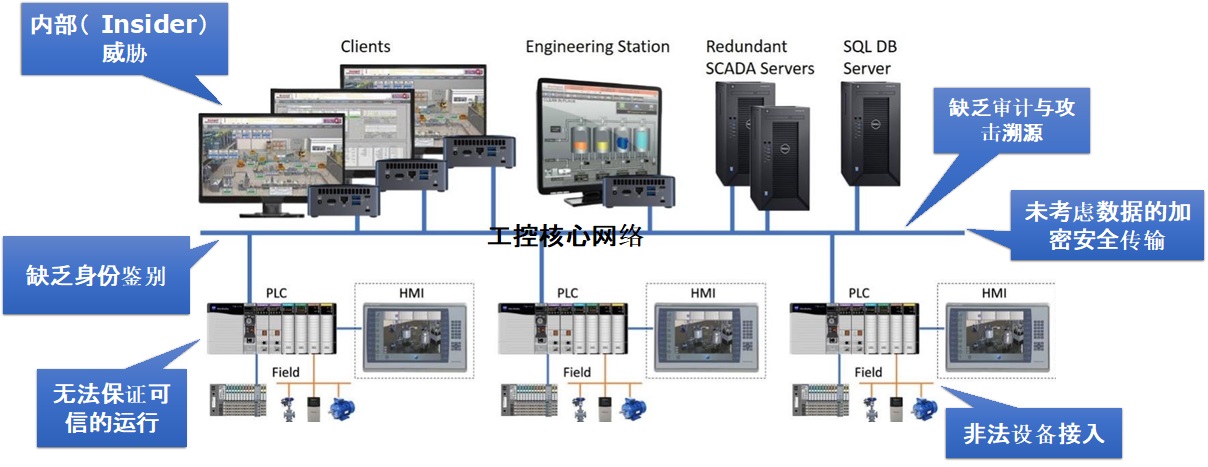
Industrial control systems generally lack security design from the beginning. The design mainly considers the real-time performance, reliability and stability of the system, sacrificing security for real-time performance. Traditional IT security solutions such as identity authentication, authorization, and encryption are not suitable for industrial control systems. There are a large number of vulnerabilities in industrial devices and protocols. According to the national CNVD statistics, as of September 2021, the number of industrial control system vulnerabilities has exceeded 3,100, while security vendors, hackers and other organizations may have far more vulnerabilities than CNVD statistics. However, key industrial devices are closed and difficult to update. These loopholes may be maliciously exploited at critical moments, resulting in production theft, monitoring, and destruction. Furthermore, the accelerated integration of IT&OT has led to the exposure of more and more security threats since the industrial control systems are changing from close to open, from stand-alone to interconnected, and more and more devices are directly exposed to attackers. This project aims to secure PLC/RTU in industrial control systems. The involved techniques include hardware secure accelerator, device fingerprinting, lightweight identity authentication, etc.
Students
Copyright © 2024 by Hao Han (as of Aug. 2024)


